Nightmare before Christmas? Patch now to avoid a cyber crisis this holiday season

This Threat Advisory was updated on 14 December 2022, following reports of vulnerability exploitation in FortiOS and Citrix appliances. On 13 December (around 0200 AEDT), Fortinet disclosed that recently patched CVE-2022-42475 is being actively exploited in limited attacks.[i] On 13 December (23:20 AEDT), the US National Security Agency (NSA) reported that CVE-2022-27518 in Citrix appliances is being actively exploited in targeted attacks by APT5.[ii] Both CVEs enable unauthenticated remote code execution (RCE).
Published by Cyber Cyber Intelligence on 12 December 2022
Prawns, family barbecues and backyard cricket aren’t the only Christmas traditions for Australian and New Zealand cyber professionals. For years, cyber threat activity has spiked during the holiday season, increasing risk when many organisations have reduced staff and paused technology programs.
Cyber risk can rise over the holiday season, especially for organisations that don’t use December to adequately prepare. Reduced staffing and technology change freezes during this time limit security teams’ ability to manage vulnerabilities, detect threats, respond to incidents and adapt to the always-changing cyber threat landscape.
Criminal and nation-state hackers don’t pause at Christmas
Cyber threat actors see these organisational challenges as an opportunity. For several years, CyberCX Intelligence has observed cyber criminals and nation-state actors rapidly weaponise vulnerabilities that are disclosed late in the year and integrate exploits for these vulnerabilities into their tool chains. As a result, cyber security incidents often increase in December and January, including through the Christmas-New Year period.
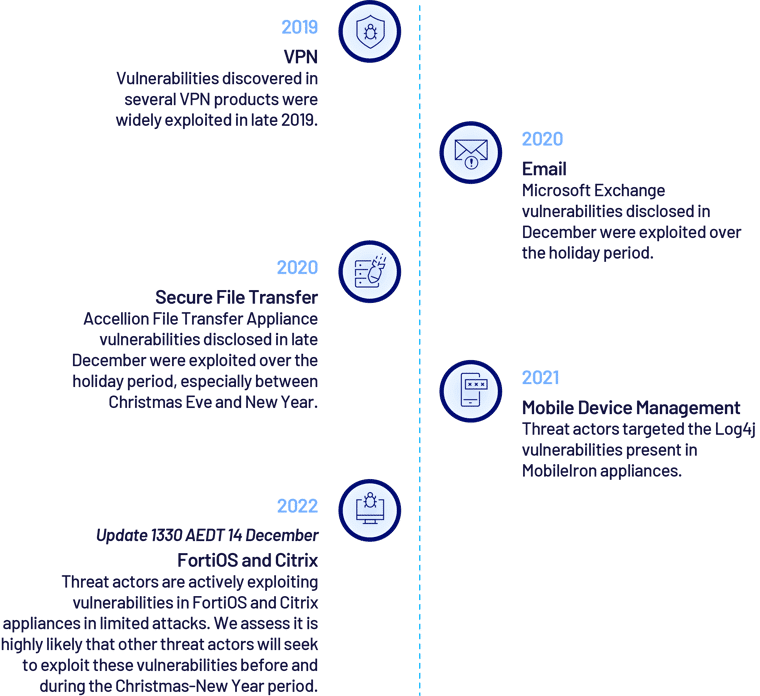
Why we shouldn’t be complacent in 2022
In 2022, CyberCX Intelligence has observed significant shifts in the Australian and New Zealand threat landscape which likely foreshadow even higher cyber risk this holiday period than in previous years.
These shifts include:
- An 88% increase in cyber extortion groups targeting Australia and New Zealand over October to December 2022, compared to July to September 2022.
- An unprecedented number of cyber extortion groups active in the region, up to at least 12 in November 2022.
- A series of high-impact data breaches in Australia since September that has exposed 1 in 2 Australians’ personal information, leaving individuals and organisations vulnerable to follow-on attacks.
- An increasingly dynamic vulnerability ecosystem, with the time between public disclosure and threat actor exploitation continuing to narrow.
- Increasing rates of supply chain attacks against managed service providers and other third parties, designed to affect organisations at scale.
Tips to protect your organisation (and your holidays)
Ensure that patching across your critical assets and systems is up-to-date
Update 1330 AEDT 14 December
Pay particular attention to internet-facing platforms such as:
- Routers, gateways and firewalls
- Web and email servers
- FortiOS versions vulnerable to CVE-2022-42475iii
- Citrix ADC and Gateway appliances vulnerable to CVE-2022-27518 (excluding for Citrix-managed appliances)iv
- We also recommend conducting threat hunts using the NSA’s guidances
Review and update your Cyber Security Incident Response Plans
At minimum, make sure your Plans:
- Identify critical roles, including:
- Who is responsible for these roles
- Alternative people who can undertake these roles if the person responsible is unavailable
- Out-of-hours contact details for all people listed as responsible and alternatives for these roles
- Have clear escalation processes
- Are stored securely, including in hardcopy, in the event that corporate IT systems are unavailable during an incident.
i https://www.fortiguard.com/psirt/FG-IR-22-398
ii https://media.defense.gov/2022/Dec/13/2003131586/-1/-1/0/CSA-APT5-CITRIXADC-V1.PDF
iii https://www.fortiguard.com/psirt/FG-IR-22-398
iv https://www.citrix.com/blogs/2022/12/13/critical-security-update-now-available-for-citrix-adc-citrix-gateway/
v https://media.defense.gov/2022/Dec/13/2003131586/-1/-1/0/CSA-APT5-CITRIXADC-V1.PDF







